New SQLBench Agent - version 2022.08.02.06
Today we announce a new release of the SQLBench Agent - version 2022.08.02.06
In this latest release, we focus primarily on making it easier for you to configure the SQLBench Agent agent with minimal permissions.
The SQLBench Agent never required high level permissions such as sysadmin or controlserver, but it was a little tricky to set up without them.
We now provide simple prompts during setup which easily guide you through minimal permission setup, and we actively discourage use of high level permissions.
TLS 1.3 security protocol is also now supported, which also requires a minimum .Net Framework upgrade to 4.7.2.
We hope you enjoy these features in our latest SQLBench Agent release!
Below is a specific list of permissions required by our latest SQLBench Agent:
Windows (SQL Server Host)
-
Membership of Windows Performance Monitor Users Group
-
Ownership of an NTFS directory for SQLTrace logging.
Windows Groups
NTFS
SQL Server
-
ALTER_TRACE
-
VIEW SERVER STATE
-
VIEW ANY DEFINITION
-
Membership of SQLAgentOperatorRole role in MSDB database
-
GRANT EXECUTE ON [msdb].[dbo].[sp_get_composite_job_info]
-
GRANT SELECT ON [msdb].[dbo].[sysjobsteps] and [msdb].[dbo].[sysjobhistory]
-
GRANT EXECUTE ON [master].[dbo].[sp_enumerrorlogs] and [master].[dbo].[xp_readerrorlog]
-
Guest access in every user database (including model database to include DBs created in future)
Server Permissions
SQLAgent
SQLErrorLog
User Databases
Implementation Script
The below script implements permissions precisely required by the SQLBench Agent
Replace the text "##SQLBenchLogin##" with the name of the SQL Server Login or SQL Server Windows Login that SQLBench will connect to the instance with.
USE [master]
GO
/* To create & manage SQLTrace logs */
GRANT ALTER TRACE TO [##LoginName##]
/* To access server level DMVs */
GRANT VIEW SERVER STATE TO [##LoginName##]
/* To access database object definitions via sysobjects etc (but not table data) */
GRANT VIEW ANY DEFINITION TO [##LoginName##]
/* To enumerate & read the SQL Error log (requires a guest user in master) */
if not exists(select * from sys.database_principals where name = '##LoginName##')
CREATE USER [##LoginName##] FOR LOGIN [##LoginName##]
GRANT EXECUTE ON [sys].[sp_enumerrorlogs] TO [##LoginName##]
GRANT EXECUTE ON [sys].[xp_readerrorlog] TO [##LoginName##]
/* To access SQL Agent Jobs & their execution history */
use [msdb]
GO
if not exists(select * from sys.database_principals where name = '##LoginName##')
CREATE USER [##LoginName##] FOR LOGIN [##LoginName##]
EXEC sp_addrolemember 'SQLAgentOperatorRole', '##LoginName##'
GRANT EXECUTE ON [dbo].[sp_get_composite_job_info] TO [##LoginName##]
GRANT SELECT ON [msdb].[dbo].[sysjobsteps] TO [##LoginName##]
GRANT SELECT ON [msdb].[dbo].[sysjobhistory] TO [##LoginName##]
GO
/* Give access to user DBs */
declare @db nvarchar(1000), @s nvarchar(1000)
if object_id('tempdb..#dbs') is not null drop table #dbs
select name into #dbs from master..sysdatabases /* where name in ('','') */
select @db = min(name) from #dbs
while @db is not null
begin
select @s = N'use ['+@db+N'];
if not exists(select * from sys.database_principals where name = ''##LoginName##'')
CREATE USER [##LoginName##] FOR LOGIN [##LoginName##]'
exec(@s)
select @db = min(name) from #dbs where name > @Db
end
GO
The SQLBench Agent has always been easy to set up, but it has also always been a little too easy to use sysadmin.
If you still prefer to use sysadmin, we won't stop you, but we now offer an easy to use visual guide to setting up minimal permissions.
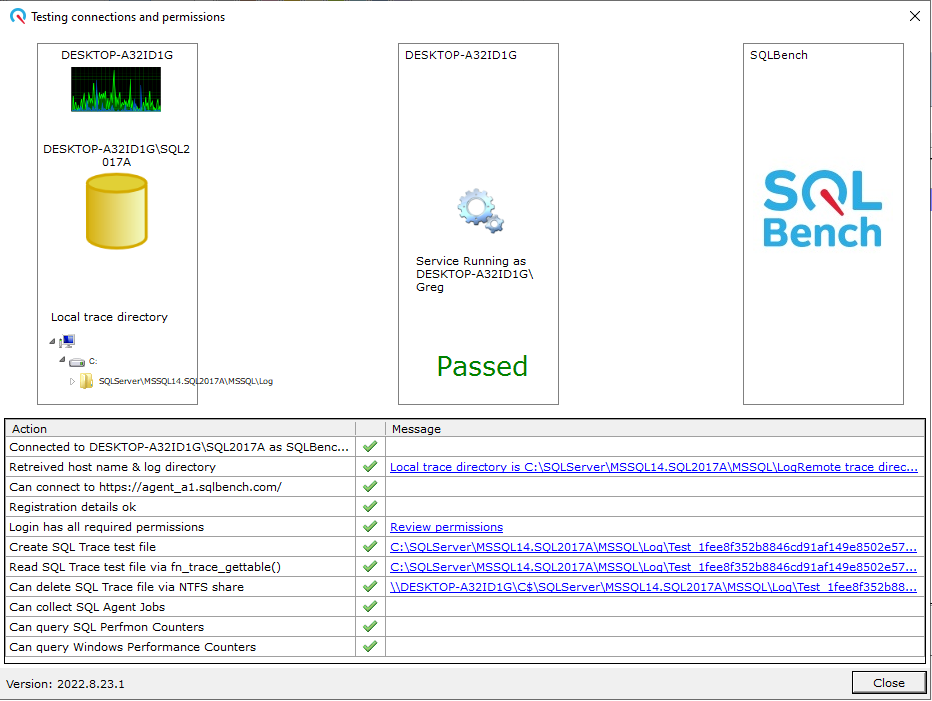
When using the SQLBench Config to connect our agent to a SQL Server instance, the "Test" process now evaluates permissions granted to the chosen SQL / Windows Login and provides visual feedback and a script to implement permissions.
Agent Connection Test Utility
When connecting the SQLBench Agent to a new SQL Server instance, click the "Test" button in the bottom right.
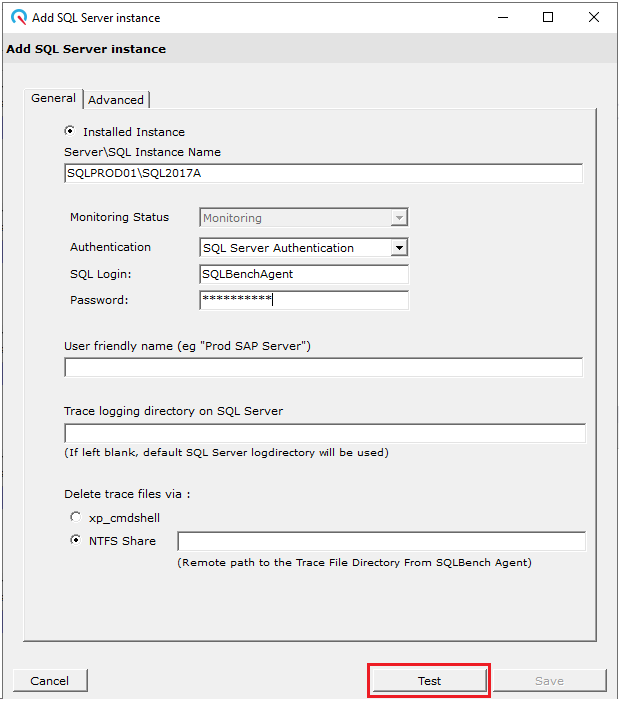
Running A Test
The test program connects to SQL Server & verifies whether required or un-necessary permissions have been granted.
If any required permissions have not been granted, or if any un-necessary permissions have been granted, the test fails with an informative message displayed.
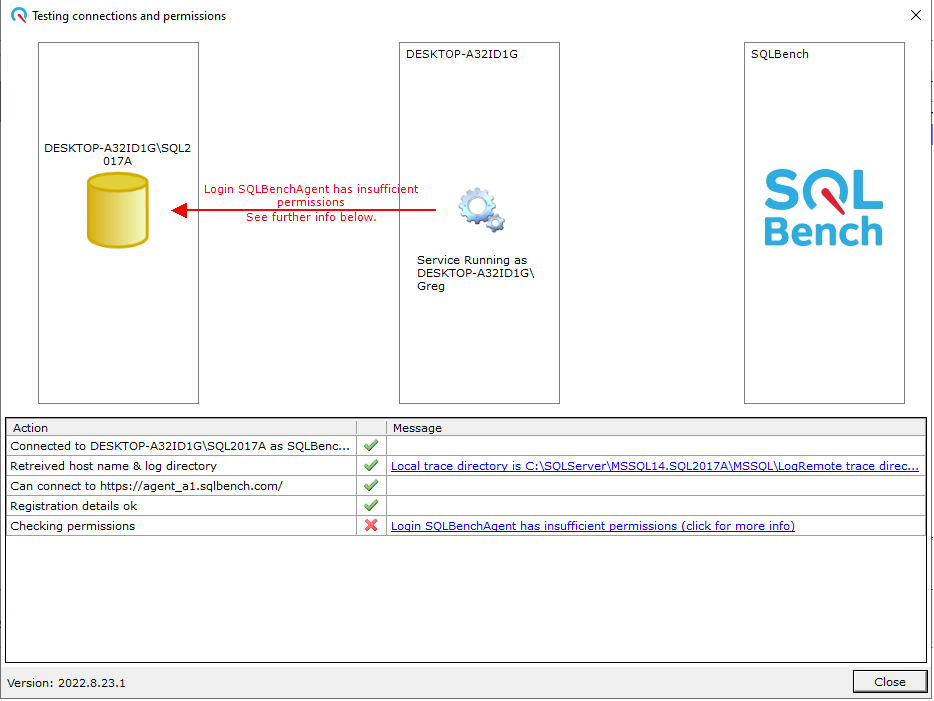
Permissions Advisor
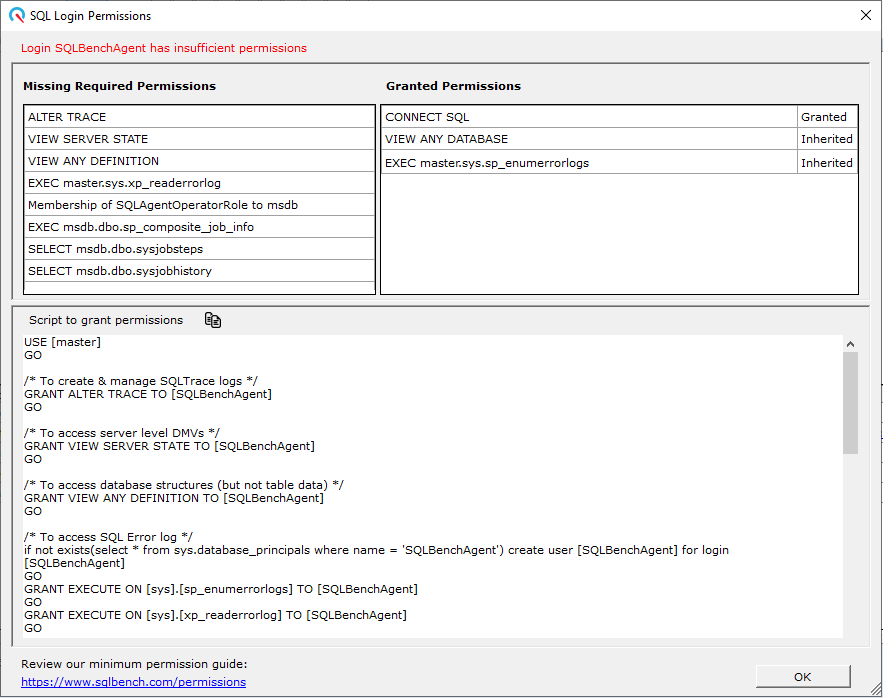
Clicking the message link pops up a list of granted & missing permissions.
A script is also conveniently provided to correct any necessary permission changes.
Minimum Permissions Passed!
When all required permissions have been assigned, your job is complete!
The SQLBench Agent can now connect to the SQL Server instance to be monitored and collect all telemetry.
SQLBench previously supported TLS 1.1 but this release now supports up to TLS 1.3
SQLBench Agent requires installation of .Net framework 4.7.2 to support TL 1.3
SQLBench now utilizes .Net Framework 4.7.2's SecurityProtocolType.SystemDefault feature which auto-selects the highest TLS level supported by the underlying system, as described in this Microsoft article
